Every day I wake up and check the technology news – as is my habit – and scroll through the headlines I’m expecting to find a marriage celebrant in there. Why?
When a couple books with us they hand over a wide amount of personal data. Then when they sign a notice of intent with us, even more.
At time of booking
A quick security audit of my customer journey says that I collect the following data on booking:
- Full names
- Email addresses
- Phone numbers
- Residential addresses
- Dates of birth
- Wedding date and venue location
- Credit card info (although by the time it gets to me, I only get the last four digits of their card number and what type of credit card it is)
- Favourite ice cream flavour (which sounds unimportant, but personable data like this helps hackers in social engineering)
- Other vendors (who are also collecting personal data on them, including photos)
At time of notice of intended marriage
Then once we start preparing a notice of intent we add in:
- clarification on full legal names,
- occupations,
- marital status, and former marriage details if previously married,
- ID numbers (passport, drivers license, birth certificate),
- parent names at birth and parent names today plus countries of birth,
- gender/gender identity,
- places of birth,
- and possibly scans/photos of ID,
- their signatures.
After their wedding
Then after you get home from their wedding and in the coming weeks:
- lots of photos of the couple and their guests,
- their wedding vows,
- more variants of their signatures,
- the names and signatures of their witnesses,
- possibly a registration number with a BDM for their marriage paperwork,
- even the ability to order a copy of their offical certificate of marriage.
If a malicious actor got their hands on that data, they can wreck havoc. They have enough data to call their mobile phone service provider and say they lost their phone, can you send a new SIM to us so they can interrupt phone calls and text messages. They have enough information to call a bank and reset an internet banking password and access funds. That hacker would have enough information to socially manipulate other people in their life to send money or take actions.
If a hacker accessed your computer, they could steal your couples’ identities. Which is bad enough if you’re a regular Joe. But what if you marry a CEO, or a politician, or a celebrity. That data is pure gold to a hacker.
You, and I, hold a great responsibility in receiving and using this data.
On top of all this, the data is most likely contained in your email account, on your computer, in a cloud storage platform. Are these secure?
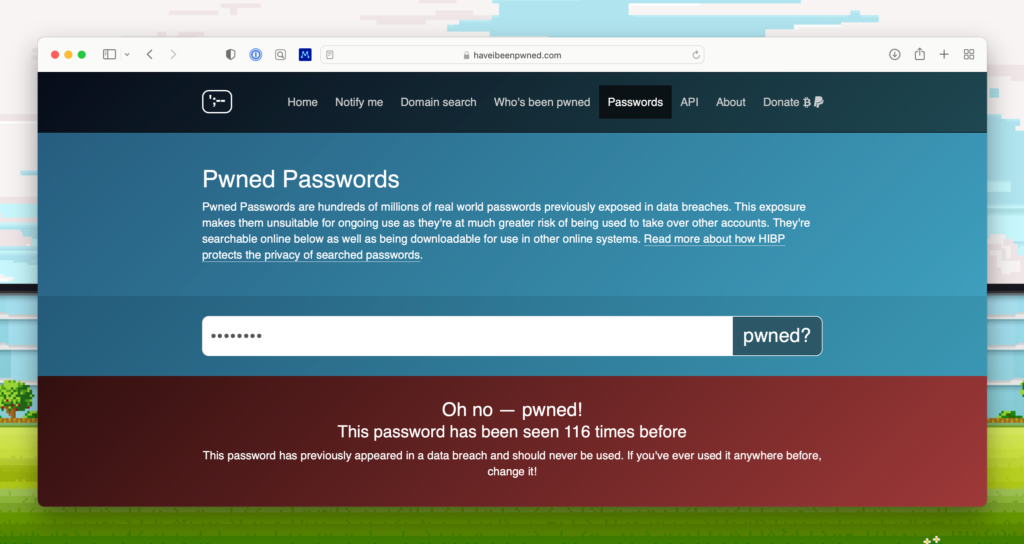
If you’re wondering whether your personal data has already been exposed in a previous hack on another company, go to haveibeenpwned.com and enter your email and then phone number to get an inside look into what private data has been made public. Then go to haveibeenpwned.com/Passwords to see if your password is original.
Let’s get secure.
Security 101 for celebrants
Here are some steps I am begging you all to take to secure yourself online.
- Step 1: Enable Multi Factor Authentication. 2FA/MFA solves most problems, it’s simply the act of having another thing on top of your username and password. Put it on your internet banking, all email accounts, website hosting, Facebook, Twitter, Instagram everything that lets you. Use 1Password, Apple Keychain, Microsoft, or Google Authenticator (some sites only use one or the other). This is the most important (and easiest) thing you can do. If there’s a choice between getting a text message 2FA code or using an authenticator app, choose the app. Text messages can be hacked more easily than the apps.
- Step 2: Use a Password Manager. I use 1Password for Teams and that costs a few dollars a month, but if you’re an Apple user the latest releases of the software have Keychain password manager built-in for free. Set it up ASAP and as you go to every website, change your damn passwords and give each service a unique password so when one service gets hacked, not all of your services are hacked. If you do one thing today it would be to use a password manager and give each important service in your business (email, website, domains, Facebook, banking, etc) a unique password.
- Step 3: Review Access. Facebook is bad at allowing 3d party apps to sign in with your account. Go to “Facebook Settings” > “settings and privacy” > “apps and websites” and kill off everything that you aren’t actively using right now. Never use Facebook or Google to log in to any website ever! Create new accounts and use your password manager to keep track. Do the same with your Google / Gmail, Youtube, Twitch, Instagram, Twitter, Apple ID, Spotify and any other “sign in using x” type account. If you have accounts like Metamask, review what has access to that (“connected sites”).
- Step 4: Adblock + Anti-Virus. Use Apple Safari or Firefox as your only browser and install “ublock origin” (and Lastpass!). Every other browser extension you should delete, unless you are 100% confident of what and who they are. For Anti-Virus,
if you’re on Windows, only one I recommend is “Windows Defender” (the built in one). The rest are questionable at
best. If you’re on Apple you don’t need Antivirus, but always be aware of what you’re installing. - Step 5: Physical Security. Who has access to your computer, tablet, and phone? Limit their access (use users accounts , passwords) so they can’t get access to your files and get breached. Don’t use free random/insecure WiFi for anything that you want kept secure. Make sure your home WiFi password is complex and isn’t advertised or given out to others. Create a guest network if you need. If a website seems suss, it probably is. Don’t log in! Don’t click any links in SMS or Emails that you absolutely weren’t expecting. Big one for spam prevention: Don’t give any company your phone number or email address unless they absolutely need it (they almost never do). Who knows where that info is going? Learn to say no to sharing your own data because you are keeping other people’s data safe. Does your computer have a secure and not-guessable password? Is your office locked?
- Step 6: Delete Garbage. Delete apps off your phone if you don’t need them. Review security permissions of the apps you
have left and kill off their access in your phone settings because they don’t need it (no background refresh, no 3rd party tracking). Do the same on your PC or Mac why do you have all that crap installed? - Step 7: Audit. Ask a nerdy friend to audit you. Ask them to try and access personal data or client data without your help, either online or in your house. Or if you really want to attack this threat professionally, you’ll want a security and privacy review or if you really want to go all out, a “pen test”. A pen test is short for penetration test, and you basically ask professional and ethical hackers to hack you, or at least, to try and hack you. They’ll report back on where your weaknesses and risks are. It can be pricey, but it can also keep you out of the news and out of court.
Friends of mine at Division 5 do a Cyber Security and Privacy Review from $3600, it’s two days work for a team of professionals. You;’ll sit down with a professional, work out data held, and where it goes, and that it’s being managed properly according to the legislation that applies. Outcomes would be reduced risk and guidance on what could be done to continue to meet obligations and avoid being compromised. [Disclosure: There’s no commercial deal here, they’re just friends, and you’re welcome to search for your own consultant].
Looking after your computer and internet security might seem like a lot of work. But imagine how much work it would be if you were hacked, and your clients’ data was leaked. New federal privacy laws could see you funded up to $2.1 million dollarydoos.
I’d change my password and get a password manager to save $2.1 million dollars.






